Imagine you’re part of a large organization, working with highly sensitive data, proprietary tools, or confidential information. Now picture what chaos might unfold if every team member, regardless of their job role, were granted equal access to the company’s entire infrastructure. Sounds risky, doesn’t it? That’s where Role Based Access Control (RBAC) comes in.
In this blog, we’re going to demystify what RBAC is, how it works, why it’s crucial for modern systems, and how tools like ZoopSign leverage RBAC to make workflows more secure and efficient. By the end of this blog, you'll clearly understand RBAC's meaning and how role based authentication can enhance security and operational control in your organization.
So, let’s begin!
What Is RBAC (Role Based Access Control)?
Role Based Access Control (RBAC) is a security model that restricts system access based on the roles assigned to users within an organization. Instead of granting permissions to individual users, RBAC assigns permissions to roles, and users are assigned to these roles. This approach simplifies the management of user rights and ensures that individuals have access only to the information necessary for their job functions.
The core components of RBAC are:
- Roles: These are defined job functions within an organization, such as "Administrator," "Manager," or "Employee." Each role encompasses a set of responsibilities and associated permissions.
- Permissions: These are the rights to perform specific operations on resources, like reading, writing, or deleting files. Permissions are assigned to roles rather than individual users.
- Users: Individuals who are assigned to roles. Their access to resources is determined by the permissions associated with their roles.
- Sessions: These are mappings between users and roles during a specific time frame, allowing users to assume different roles as needed.
In simple terms, Role Based Access Control (RBAC) is a security framework that restricts or grants access to data, systems, or applications based on the role of a user. It’s a system where permissions are tied to specific roles within an organization, and those roles are then assigned to individuals based on their job responsibilities.
For example:
- The HR team in a company might have access to employee records but not to financial reports.
- Developers might have access to the development environment but not to production servers.
- The CEO might have access to all high-level reports but not necessarily to back-end configurations.
This segregation ensures that people only access what they need to perform their duties—nothing more, nothing less.
How Do RBAC Roles Define Access and Permissions in an Organization?
At the heart of RBAC lies the concept of roles. But what are roles, and how do they function?
A "role" is essentially a collection of permissions that define what a user can and cannot do within a system. For example, roles may include:
- Administrator: Full permissions—can access, modify, and manage everything.
- Manager: Permission to view and analyze documents but may not have editing rights for all elements.
- Employee: More restricted access, limited to their specific tasks and responsibilities.
- Guest: Minimal access, often read-only permissions to a limited part of the system.
By associating roles with users, you eliminate the need to assign permissions on an individual basis. Instead, you map roles to users—creating a more structured and manageable system.
How Does RBAC (Role Based Access Control) Work?
The RBAC meaning may sound straightforward, but implementing it correctly involves a well-thought-out structure. Here’s how it works in practice:
- Identifying Roles: Determine all the roles within your organization and map out the duties and responsibilities tied to each role. For example, roles might differ for IT sector, HR sector, finance sector, and customer service teams.
- Defining Permissions: For each role, define the level of access required. Think about what resources or information specific roles need to do their jobs effectively.
- Assigning Users to Roles: Once roles and permissions are established, assign employees or team members to the roles that reflect their job functions.
- Continuous Monitoring: An effective RBAC system isn’t static. Regular monitoring of roles, permissions, and user assignments is critical to ensure security and efficiency.
For example, tools like ZoopSign—which specializes in custom workflows and secure access management—use RBAC security principles to ensure that only authorized team members can view, edit, or approve documents in the signing process.
Why Is RBAC Security Important for Modern Businesses?
The importance of RBAC cannot be overstated, particularly in cybersecurity. Here's why it’s essential for modern organizations:
1. Your workflow security gets enhanced
At its core, RBAC cyber security ensures sensitive data and systems are accessed only by authorized individuals. By limiting who has access to what, RBAC minimizes the risk of accidental or malicious data breaches.
For example, an entry-level employee in your support team shouldn’t have access to highly sensitive financial data. With role based authentication, you can ensure that access is securely restricted based on the user’s role.
2. Your digital compliance is simplified
Many industries are subject to strict regulatory requirements for data privacy, such as GDPR, HIPAA, or SOC 2 compliance. By leveraging RBAC security, organizations can maintain robust audit trails and ensure compliance with regulations.
3. Your workspace productivity is improved
Assigning permissions to roles instead of individuals significantly reduces administrative overhead. Plus, employees can get the access they need from day one, without endless requests to IT for permission updates.
For instance, ZoopSign allows teams to craft custom workflows, tailoring access permissions per the organization’s RBAC framework. This helps businesses stay efficient while remaining secure.
4. Your team errors are limited
Manual allocation of permissions can lead to errors or oversights. With RBAC, access control becomes systematic, minimizing the chances of someone unintentionally gaining more permissions than they need.
What Are the Real-World Applications of RBAC in Different Industries?
RBAC is not just a concept—it’s actively used in industries and businesses of all sizes. Below are some real-world applications of RBAC roles :
1. Healthcare
Hospitals and healthcare providers use RBAC to protect sensitive patient information. For instance:
- Doctors can access patient medical records for treatment.
- Nurses can view and update patient charts but not financial billing information.
- Administrative staff can handle billing without accessing medical histories.
2. Finance
In banking, RBAC security safeguards customer financial data:
- Loan officers can access loan applications but not savings account details.
- Financial advisors can view portfolio information but cannot initiate transactions.
3. IT Environments
In IT, role based authentication ensures that developers, system administrators, and other professionals only have access to environments necessary for their day-to-day work.
4. Legal and Document Management
Platforms like ZoopSign that facilitate secure digital signatures and documentation often implement RBAC cyber security to grant selective access to users. For example:
- Team A signs off on a contract.
- Team B reviews it but cannot overwrite or modify it.
- Admin roles maintain control of the document lifecycle.
In this way, RBAC roles help maintain transparency, keep processes efficient, and enhance collaboration without compromising data security. To know about folder security features, click here.
How Does RBAC Compare to Other Access Control Models?
You may have heard of other access control systems, such as Discretionary Access Control (DAC) or Mandatory Access Control (MAC), and wondered how these differ from RBAC. Here’s a simplified comparison:
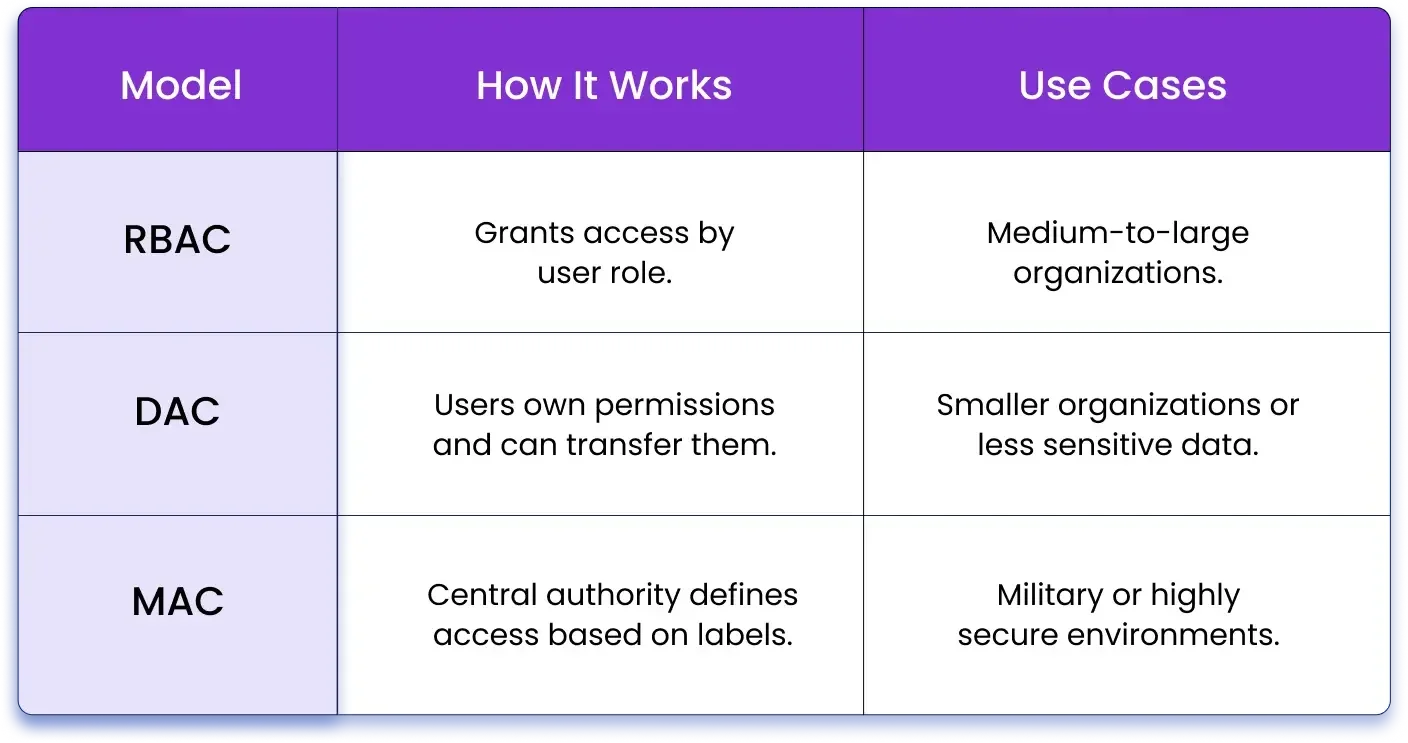
What Are the Challenges and Best Practices for Implementing RBAC?
While Role Based Access Control (RBAC) offers numerous benefits, its implementation isn’t always straightforward. Here are some common challenges and best practices:
Challenges:
- Role Explosion: Creating too many roles can make the system overly complex and counterproductive.
- Role Drift: Over time, users may retain access to roles they no longer need, posing a security risk.
- Initial Setup: Identifying roles and assigning permissions requires upfront planning, which can be time-consuming.
Best Practices:
- Start Simple: Begin with a set of basic roles and expand as your organization grows.
- Regular Audits: Periodically review roles, permissions, and user assignments to avoid outdated access.
- Use Tools Like ZoopSign: Platforms with built-in RBAC security capabilities make it easier to manage roles, permissions, and workflows without overwhelming your team.
How Does ZoopSign Use RBAC Roles for Secure Document Workflows?
ZoopSign is a trusted e-signature and document workflow solution that incorporates RBAC roles seamlessly into its platform. With features like custom workflows, ZoopSign lets organizations define who can view, edit, and approve documents—helping teams collaborate securely and efficiently.
For example:
- Access Control: Assign specific permissions to users based on their role in the document workflow.
- Audit Trails: With this Audit trail features you can Maintain a clear record of who accessed and edited the document.
- Custom Workflows: Tailor the process to match your organization’s specific needs, ensuring compliance with your RBAC security framework.
By adopting tools like ZoopSign, businesses can enhance cybersecurity measures while streamlining document workflows.
Conclusion
So, what is RBAC? It’s not just a technical security metric—it’s a cornerstone of modern business operations. By implementing Role Based Access Control, organizations can enhance their security posture, achieve compliance, and operate more efficiently.
Whether you’re running a small business or managing a large enterprise, RBAC is a must-have for securing sensitive systems, data, and workflows. And if you’re looking for a tool that helps manage roles effectively while simplifying secure document workflows, look no further than ZoopSign.
Start leveraging RBAC cyber security today to safeguard your organization and create a more structured, productive work environment. Who knew that defining roles could bring such substantial benefits?
